Introduction
The question of whether to prioritize our right to choose who gets to access our personal information and in which way or whether to prefer our right to be protected from external threats to our security has come to the public’s eye concurrently with technology’s development in the recent years. Indeed, as our devices increase in functionality and capacity, our sphere of privacy seems to decrease simultaneously. This is not to say that in order to be connected to the outside world we are forced to sacrifice our personal information, however, this is about how the debate on this topic has been influenced amongst the media and academics.
Chronology of this controversy
In this section, we chose the most characterizing events in the United States which have shaped our controversy and its debate significantly.
- 1890: First publication on the promotion of Privacy by Samuel Warren and Louis Brandeis: The Right To Privacy, Harvard Law Review 193.¹
- 1980s: (when Commercial Internet service providers first appeared) The Internet revolutionized the way we share information which has had its implications on our privacy.²
- 2001: Foundation of the National Cyber Security Alliance (NCSA), a public-private partnership aimed at raising awareness on cybersecurity for all types of users from home users to businesses.
- 11.09.2001: Al-Qaeda’s attacks on the US, peaked by the World Trade Center tragedy which increased the US government appetite for private data.
- 2008: Data Privacy Day: event practiced in 50 countries whose primary focus is on social networking and how the latter can spread private information without someone’s consent nor knowledge.
- 2013: Edward J. Snowden from the National Security Agency unveils the agency’s activities in gaining user data in questionable manners.
- 2015-2016: Federal court order issued asking Apple to unlock one of the San Bernardino mass shooting’s attacker’s Iphone to which Timothy Cook, Apple’s CEO, objected to, defending his stance to the right to privacy.
Main Actors and their position on this controversy
As we can already gather from the major events which have occurred in relation to our controversy, many actors can be linked to the subject of privacy and security as well as from a variety of sectors.
- The National Security Agency. Before establishing their position on this controversy, we think it relevant to first define what their role consists of. The latter can be divided into two distinct functions. The first, called SIGINT, consists in gathering knowledge and informing US policymakers and military forces on “electronic signals and systems used by foreign targets, such as communications systems, radars, and weapons systems” (nsa.gov). The second main role the NSA must attend to is cybersecurity, which comes down to ensuring the protection of computer systems from any kind of damage or misuse of the services they offer. In light of this information, the NSA’s position on the matter of security and privacy can more clearly be established. The following statement made in response to allegations about NSA operations gives a clear indication of their stance on what should be prioritized: “…NSA’s activities are focused and specifically deployed against – and only against – legitimate foreign intelligence targets in response to requirements that our leaders need for information necessary to protect our nation and its interest.” (NSA, July 30, 2013, Release No: PA-027-18). This remark illustrates their overall position on the matter placing the national security at the heart of all their activities and interests, therefore, siding with security over privacy without explicitly saying so.
- Private Companies can see both sides of the story as they are usually catering to their users’ needs but they can also be hired by governments or other entities whose agenda might differ from the company’s users. Either these private companies will side with the general public such as Apple, concerned with their overall reputation and branding (i.e. San Bernardino case of 2015 mentioned above in major events) or they will support the government and associated intelligence agency requiring them to provide private data from their users such as the recent event of Cambridge Analytica, a firm headed by one of Donald Trump’s election team-members in 2014 which gathered information on millions of Facebook profiles of US voters and used them to influence choices at the ballot box. For these reasons, their position cannot be so clearly determined as they differ from one to the next.
- Judicial System. From the plethora of government actors which are involved in this controversy in way of the other, apart from security agencies, the other most important actor is the branch of the judiciary. The courts and legal framework has to keep a balance between national security and individual’s rights. For example, after the revelations by Snowden, two judges in two different rulings reached opposite consensus regarding the collection and use of private data by NSA. Such events uncovered the larger problems that the judiciary is not able to grapple the pace with which technology is advancing and how it is impacting as well as changing our society. In 2015, the US government came up with USA Freedom Act amending the archaic FISA act to establish a new framework when private data is being accessed and every time a judge approval is required with the reasonable ground on the importance of call record.
- The General Public. This actor is indeed at the heart of the debate as being in a democratic context their manifestation can be of great influence on the direction of the controversy itself. Indeed, post-Snowden episode, the public became, in general, more careful with their handling of personal information. As stated by George Gao, writer for Pew Research Center: “a majority of Americans oppose the government collecting bulk data on its citizens, and two-thirds believe there aren’t adequate limits on what types of data can be collected.” (Fact Tank: News in the Number, 2015).
The following table collected by PEW Research Center can illustrate the overall trends of the general public.
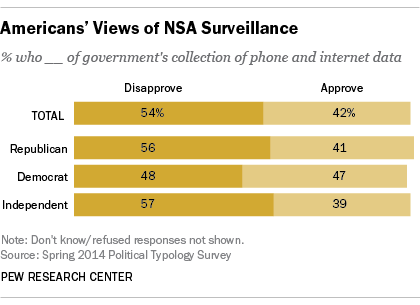
Indeed, the numbers shown indicate a slight preference for preserving privacy than providing access to people’s personal information by the NSA.
The following graph from Pew Research Center measures the public’s position on our controversy more narrowly by asking the question of “what concerns you more about the government’s anti-terrorism policies ?” from 2004 until 2016.
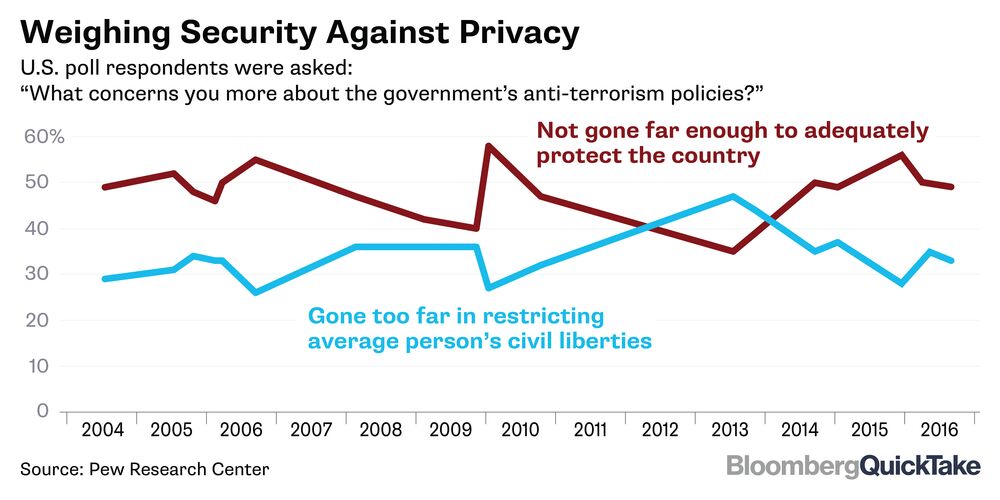
As we can observe, around Snowden’s revelation of the NSA activities in 2013, the privacy concerned citizens rose in number, however, this trend quickly went back to its original number of 30%. The graph shows us conflicting information next to the previous table as there seems to be a majority of people leaning towards an increase in security measure rather than privacy.
The stakes of the controversy for each actor and their position on these stakes
The above chapter dealt with which various actors are important and have stakes in this complex controversy. Now let’s delve deeper into why these actors are so important and what are the parts of this web in which they are involved in and care for.
As our controversy illustrates, post 9/11, the security agencies of national governments and multinational intelligence alliances had a clear mandate of keeping the country safe through their covert and overt operations. Due to the advancement of technology, the security agencies had to deploy large meta-data collection systems in order to intercept communications. As clearly seen from this development that the primary issue is national security but with the unfiltered collection of data, a mammoth problem unfolds for the other important actor represented by ‘the citizens’. Due to this data collection, an individual’s private information and activities are and can be captured without proper consent which in turn violates the fundamental right of privacy. Apart from individuals, private companies are a major source of data which naturally requires responsible involvement from their side but the important distinction for private entities in comparison to citizens is that the former keeps their organization’s interest at stake which can be or cannot be aligned with individual’s interest at large. As explained in the above chapter, the involvement of judiciary bodies is highly important since it is the custodian of fundamental human rights as well as in the implementation of national security laws.
Conclusion
Can we thus answer the still polemic question of which, if any, issue predominates over the other? Should we provide all the necessary personal information to the legitimatized actors in the name of security or should we act in the name of privacy and preserve all information that can be linked to our personal life. As we could observe from the listed events above, the controversy’s status is linked to the news occurring and affecting the general public whose reaction can be a defining factor. Having said that, there are recommendations that we as academics could suggest in order to respect both perspectives. Examples include advancing privacy driven technology and communication anonymizing tools or even promoting the accountability of security agencies by judicial bodies.
Bibliography
BRANDEIS, Louis et WARREN, Samuel. The right to privacy. Harvard law review, 1890, vol. 4, no 5, p. 193-220.
Cadwalladr C. and Graham-Harrison E. (2018). Revealed: 50 million Facebook profiles harvested for Cambridge Analytica in major data breach. The Guardian. (online). Available at: https://www.theguardian.com/news/2018/mar/17/cambridge-analytica-facebook-influence-us-election (Accessed 10 May 2019)
Congress.gov. (2015). H.R.2048 – USA FREEDOM Act of 2015 (online). Available at: https://www.congress.gov/bill/114th-congress/house-bill/2048 (Accessed 10 May 2019)
Gao, G., (2015). What Americans think about NSA surveillance, national security and privacy. Pew Research Center. (online). Available at: https://www.pewresearch.org/fact-tank/2015/05/29/what-americans-think-about-nsa-surveillance-national-security-and-privacy/ (Accessed 10 May 2019)
Lichtblau, E. and Benner, K. (2016). Apple Fights Order to Unlock San Bernardino Gunman’s iPhone. The New York Times. (online). Available at: https://www.nytimes.com/2016/02/18/technology/apple-timothy-cook-fbi-san-bernardino.html (Accessed 10 May 2019).
Lindsey N. (June 2018). Data Privacy Day 2018 Comes at an Important Time in the Privacy and Security Debate, (online). Available at: https://www.cpomagazine.com/data-privacy/data-privacy-day-2018-comes-at-important-time-privacy-security-debate/ (Accessed 20th May 2019)
Liptak, A. and. Schmidt, M.S. (2013). Judge Upholds N.S.A.’s Bulk Collection of Data on Calls. The New York Times. (online). Available at: https://www.nytimes.com/2013/12/28/us/nsa-phone-surveillance-is-lawful-federal-judge-rules.html?_r=0 (Accessed 20 May 2019)
National Security Agency | Central Security Service. Mission and Values. (online). Available at: https://www.nsa.gov/about/mission-values/ (Accessed 20th May 2019)
National Security Agency | Central Security Service. NSA Press Statement in response to allegations about NSA operations. (online). Available at:https://www.nsa.gov/news-features/press-room/Article/1618731/nsa-press-statement-in-response-to-allegations-about-nsa-operations/ (Accessed 10 May 2019)
Noble, J. (2013). U.S. debates security vs. privacy 12 years after 9/11, USA Today. (online). Available at: https://eu.usatoday.com/story/news/nation/2013/09/10/us-debates-security-vs-privacy-12-years-after-911/2796399/ (Accessed 20th May 2019)
Stay Safe Online: National Cyber Security Alliance. About Us Empowering a Safer Digital World. (online). Available at: https://staysafeonline.org/about/ (Accessed 20 May 2019)
Strohm C. (2017). Privacy Vs. Security. Bloomberg. (online). Available at: https://www.bloomberg.com/quicktake/privacy-vs-security. (Accessed 10 May 2019)
Tam, P.W. (2016). Privacy vs. Security, Battle Lines Drawn. New York Times. (online). Available at: https://www.nytimes.com/2016/02/19/technology/privacy-vs-security-battle-lines-drawn.html (Accessed 10 May 2019)
